Java Generate 256 Bit Key
AES uses the same secret key is used for the both encryption and decryption. Unlike AES 128 bit encryption and decryption, if we need a stronger AES 256 bit key, we need to have Java cryptography extension (JCE) unlimited strength jurisdiction policy files. GenerateDataKey returns a unique data key for each request. The bytes in the key are not related to the caller or CMK that is used to encrypt the data key. Use AES128 to generate a 128-bit symmetric key, or AES256 to generate a 256-bit symmetric key. AWS SDK for Java. AWS SDK for JavaScript. AWS SDK for PHP V3. Encryption Key Generator. The all-in-one ultimate online toolbox that generates all kind of keys! 64-bit 128-bit 256-bit 512-bit 1024-bit 2048-bit 4096-bit.
Spring jdbc auto-generate primary key. If you are poor chap like me, below code should make your life easy.
Generate 256 Bit Key
Chilkat • HOME • Android™ • Classic ASP • C • C++ • C# • Mono C# • .NET Core C# • C# UWP/WinRT • DataFlex • Delphi ActiveX • Delphi DLL • Visual FoxPro • Java • Lianja • MFC • Objective-C • Perl • PHP ActiveX • PHP Extension • PowerBuilder • PowerShell • PureBasic • CkPython • Chilkat2-Python • Ruby • SQL Server • Swift 2 • Swift 3/4 • Tcl • Unicode C • Unicode C++ • Visual Basic 6.0 • VB.NET • VB.NET UWP/WinRT • VBScript • Xojo Plugin • Node.js • Excel • Go
Installing OpenSSLThe first thing to do is to make sure your system has OpenSSL installed: this is a tool that provides an open source implementation of SSL and TLS protocols and that can be used to convert the certificate files into the most popular X.509 v3 based formats. Ssl generate key from crt. The conversion process will be accomplished through the use of OpenSSL, a free tool available for Linux and Windows platforms.Before entering the console commands of OpenSSL we recommend taking a look to our – CER, CRT, PEM, DER, P7B, PFX, P12 and so on.
Generate 128 Bit Key Java
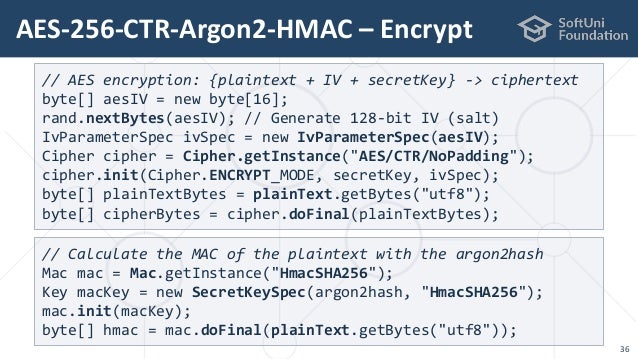
| Discusses symmetric encryption key generation techniques for block encryption algorithms such as AES, Blowfish, and Twofish, or for other algorithms such as ChaCha20.
| |||||
© 2000-2020 Chilkat Software, Inc. All Rights Reserved.
Mar 12, 2020 Use the OpenSSL command-line tool, which is included with InfoSphere MDM, to generate AES 128-, 192-, or 256-bit keys. The madpwd3 utility is used to create the password. Using a key derived from a password hash means someone could brute force this using either a known list of passwords or dictionary. Since SHA-256 is quite fast, it's very easy to do with a moderate amount of computational power. To better protect the key from such an attack, it is suggested to use a password derived from a key derivation function. Apr 03, 2020 A cryptographic hash can be used to make a signature for a text or a data file. In this tutorial, let's have a look how we can perform SHA-256 and SHA3-256 hashing operations using various Java libraries. The SHA-256 algorithm generates an almost-unique, fixed-size 256-bit (32-byte) hash. This is a one-way function, so the result cannot be.